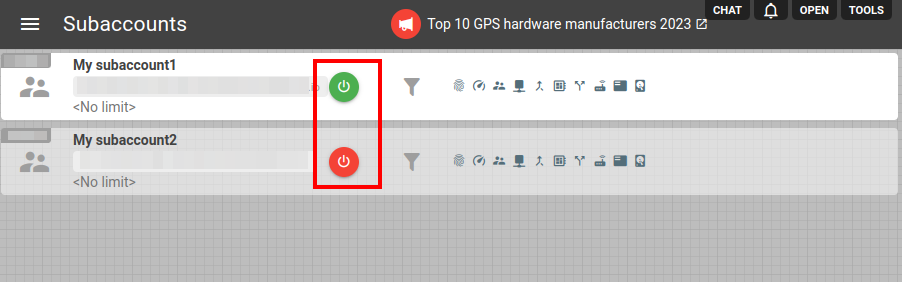
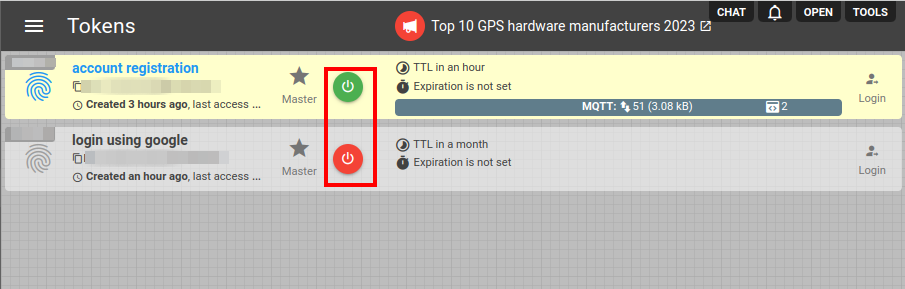
We are excited to introduce a highly requested feature in today's update. Managing projects with complex architectures, numerous subaccounts, and intricate token systems can be challenging. In response to user feedback, we've now made it easier for you to temporarily suspend subaccount activities.
Previously, achieving this required setting a completely restricted limit for the subaccount. However, with the latest update, you can now simply toggle the ON/OFF switch for the desired subaccount or token. Notably, disabling this option will recursively affect all nested subaccounts.
REST API method to disable subaccount:
PUT /platform/subaccounts/{subaccount-id}
Payload: {"enabled": false}
Similarly, to disable a token, use the following REST API call:
PUT /platform/tokens/{token-id}
Payload: {"enabled": false}